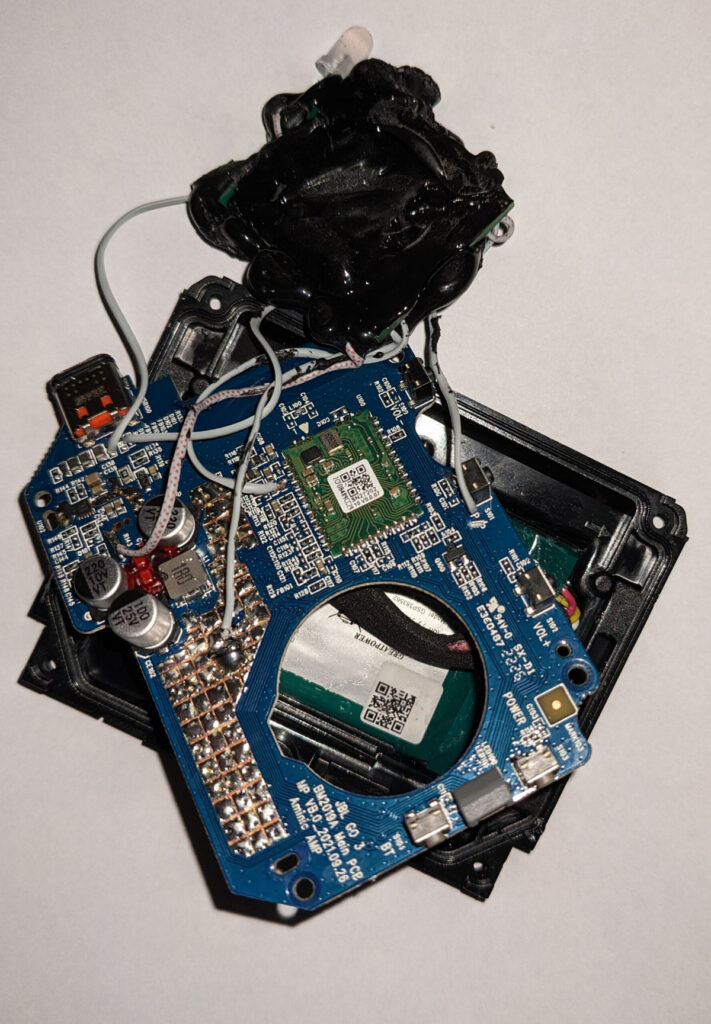
A new form of carjacking has been discovered by UK-based automotive cybersecurity researcher Ian Tabor, which allows thieves to break into keyless vehicles using a special hacking tool to spoof the security system. One particular version of this device, he noted, could appear as a seemingly harmless portable speaker from JBL.
What led to Tabor researching the matter was actually caused by his own experience of losing his Toyota RAV4 last year. The first few attempts of the theft were even documented by the researcher on Twitter, where he assumed that these were merely acts of senseless vandalism on his car. More specifically, Tabor tweeted that vandals have torn off its front left-side bumper and partially dismantled the headlight not once but twice in three months.
Why do I bother having a nice car? I know it's a first world problem but can who ever it is just leave my fcuking car alone. No lights on the way to work this morning and even more gashes in the paint work and the moulding has no clips any more. Not happy. https://t.co/a8ddBISUDy pic.twitter.com/qzWywUaW3E
— Ian Tabor – CAN injection 🚘💉 (@mintynet) July 19, 2022
The third time, unfortunately, was the charm for the thieves as the RAV4 went missing a few days after the second attempt. This incident prompted Tabor to investigate how his car was stolen, together with fellow automotive security expert Dr. Ken Tindell. Their findings have been published as a detailed report via the latter’s Canis Automotive Labs blog on Github.
In their research, it is discovered that the carjackers are using a new and sophisticated approach called CAN (Controller Area Network) Injection, which exploits a newly found vulnerability in 2021 Toyota RAV4 vehicles dubbed as CVE-2023-29389. This particular flaw automatically trusts messages from other ECUs (electronic control units), allowing physically proximate attackers to drive a vehicle by accessing its CAN bus and then sending a forged key validation message. However, thieves are first required to pull away the bumper in order to expose the car’s headlight connector to access the ECU, hence the presumed vandalism attempts.

What’s even more concerning is that such methods, which have been documented on video by the way (shown above), would reportedly take only two minutes to break into keyless vehicles. Upon further digging on Youtube, crime forums and even the dark web, Tabor discovered that thieves have been using CAN Injection tools that are sold online as emergency start devices. These are originally intended for use by owners or automotive professionals when a car’s key fob is lost, stolen, or otherwise unavailable.
As mentioned earlier, one version of this hacking tool, which both security experts purchased for reverse engineering purposes, came in the form of a fake JBL portable speaker – a disguise that can easily fool any unsuspecting individual or authority if uninspected. Our own research has found that other similar tools are also available as generic key fobs and, of all things, a certain retro handset. Of course, we won’t link our discoveries here due to obvious reasons, and we do not condone the use of such equipment.
According to Tindell, pressing the play button on the fake JBL portable speaker will trigger it to send out a CAN message burst that instructs the targeted vehicle’s ECU to unlock its doors. Of course, with the car believing that the false key is valid, thieves are also given access to its Push Start function and are able to drive off.
While the attack was successfully replicated on a Toyota RAV4, it is still possible that something similar could occur on other vehicles using the same technology and architecture. Tabor and Tindell have alerted Toyota regarding the vulnerability, but have yet to receive any acknowledgement or response from the automaker.
(Source: Ian Tabor [Twitter], via ArsTechnica / Canis Automotive Labs)
Follow us on Instagram, Facebook, Twitter or Telegram for more updates and breaking news.