Reports of a new rootkit that allows hackers to hide malware within GPU memory are beginning to surface. The most recent news was reported by Bleeping Computers, who allegedly discovered the rootkit being peddled across several of these forums.
Specifically, the hackers were selling a proof-of-technique concept that enables threat actors to store their malicious code within the GPU memory buffer, instead of hiding it within the RAM, as most malware is typically hidden. Doing this enables the malware to stay hidden from antivirus software, as said programs usually do not scan the memory buffer of the GPU.
This isn’t the first time that a malware of such nature has been created either. Six years ago, a hacker group called Team Jellyfish create the world’s first GPU-based malware, aptly named JellyFish. The rootkit was Linux-based and served as the foundation of other GPU-based rootkits that exist on the market.
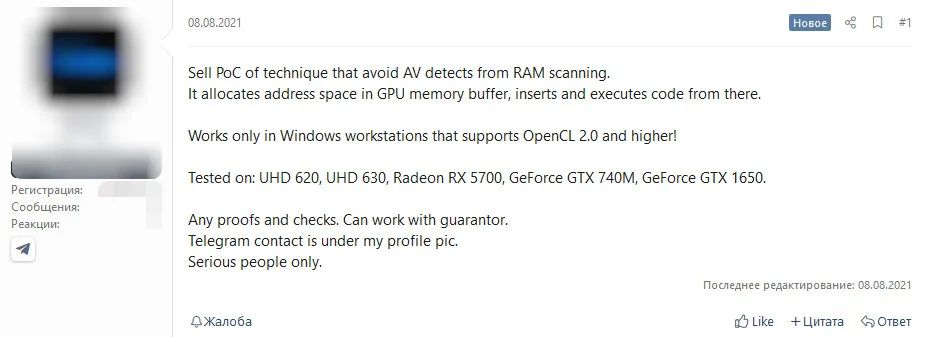
As for which GPU the rootkit works on, the seller says that it only works on Windows systems supporting Open CL 2.0. In addition, the GPUs that were tested with the rootkit include Intel’s UHD 620 and 630 integrated graphics, NVIDIA’s GeForce GTX 740M, GTX 1650, and AMD’s Radeon RX 5700.
At the time of writing, the code had already been sold and that the seller is preparing a demonstration, in order to show how it works publicly.
(Source: Bleeping Computers via KitGuru)
Follow us on Instagram, Facebook, Twitter or Telegram for more updates and breaking news.


