Its close to 3 weeks now since Malindo Air first confirmed that they had suffered a massive data breach affecting millions of it’s passengers’ personal information. Since then, the Airline has published a number up updates in relation to the breach – the last of which was released on the 23rd of September claiming that the breach has been ‘contained’ and two unnamed former employees of its e-commerce provider GoQuo (M) Sdn Bhd had improperly accessed and stole their data.
On the 27th of September, Malindo sent out a similar email to all its customers with no further explanation as to the cause or the severity of the breach. The email only cautioned customers to be wary of any suspicious and unsolicited calls or emails – and reminded them that their passwords have been auto-reset.
What Malindo Air should have done is inform affected customers on the severity of the breach and what kind of remedial action is available to them. They did not. While it is already known that Customer’s personal contact details as well as Passport information was leaked together with their flight booking details – it was assumed that these were limited to only historic flight bookings. Unfortunately, we can now independently confirm that advance flight booking information was also included in the leaked files.
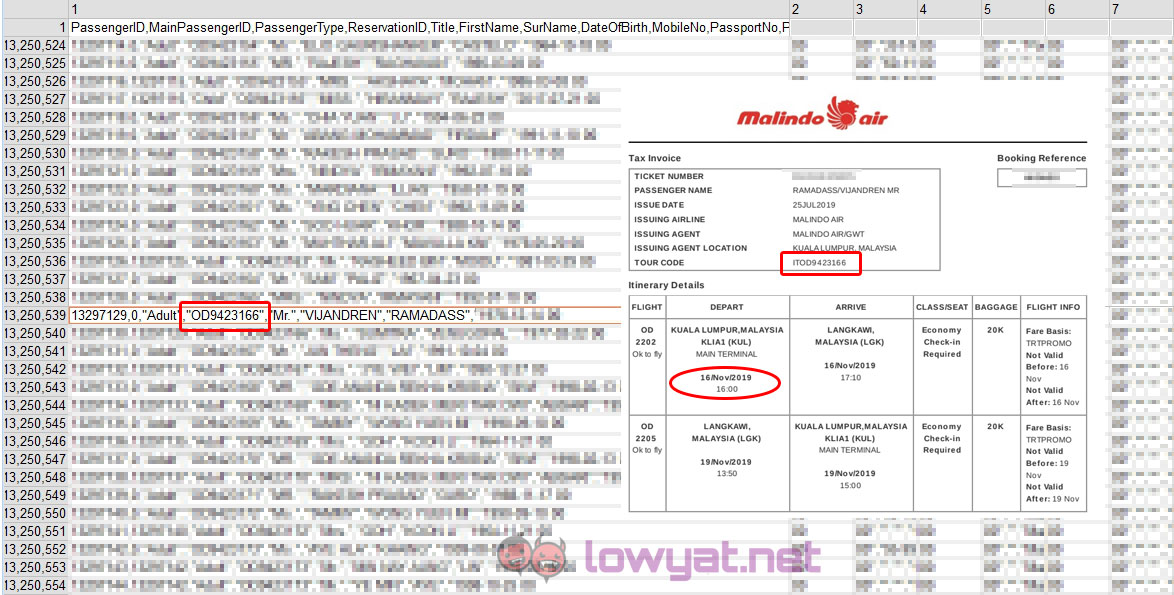
While there is very little risk associated with the historical travel information, advance flight bookings details could be easily misused and manipulated by anyone who has access to the leaked files. This information puts travelers at risk as their future travel details and dates have been leaked out. We’re not even going to get started on the number of Datuk, Datin’s and Tan Sri’s who are on the leaked list who would not be too happy to have their travel privacy exposed. Malindo Air should be notifying all those affected – as the possibility of this information being abused is a lot higher compared to a trivial password auto-reset.
The Real Cause of the Data Breach
Malindo Air, in their last statement have blamed the Data Breach on two ‘unnamed’ ‘former’ employees for improperly accessing and ‘stealing’ the data. While we are fairly certain someone at Malindo Air did make a huge blunder leading to the breach – we’ve got enough reason to believe that the underlying cause was a poorly configured security setting on their Amazon S3 bucket. Amazon’s S3 security settings is something that can be tricky at times and has unfortunately been the reason behind a number of high profile data breaches in the last couple of years (read more here).
While most of the reports on the breach so far have been based off the dumping of 4 files on the darkweb as well as on file sharing platforms, there are about 18 backup files of information that were siphoned off the Amazon S3 bucket that was left open to public access. The bucket in question, which still remains active today (albeit with properly configured security settings) is at https://sunstarcms.s3.amazonaws.com. Sun Star CMS is the name of the e-commerce system utilized by Malindo Air on their online booking site.
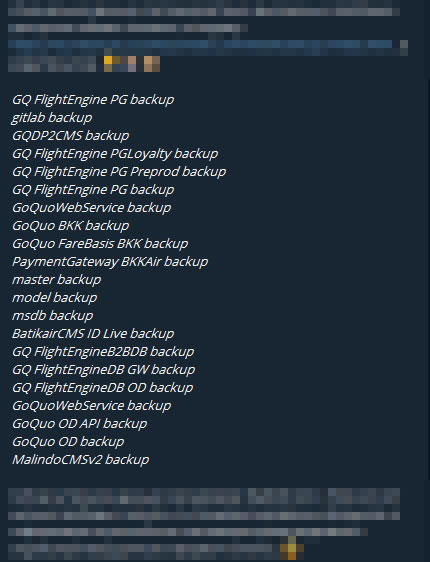
Malindo Air has at this point in time not released any further information as to the contents of the above files, as well as whether login credentials stored in these files were encrypted or not. It is fairly obvious that the backup files containing the Flight and Passenger information was not encrypted. Based on the booking dates present in the backup files, we can also independently confirm that the backup was done sometime between late August and early September 2019. Malindo Air has only confirmed that no payment information were stored in any of the leaked files.
We are hoping that Malindo Air will be taking the necessary steps to inform all affected customers, especially those with upcoming flights to be extra vigilant as their upcoming flight information and travel plans have been leaked in the data breach.
Follow us on Instagram, Facebook, Twitter or Telegram for more updates and breaking news.



