It looks like Logitech may have to revisit the design and build of its USB wireless receiver technology for its keyboards and mice. Especially after a security researcher discovered several vulnerabilities that hackers could potentially use to exploits systems via the dongle.
The security flaws were reported by a Marcus Mengs (@mame82), who posted his discovery of the flaws and how they work on both Twitter and YouTube. In total, Mengs discovered four new vulnerabilities in Logitech dongles featuring the brand’s “Unifying” 2.4GHz radio technology. It’s an alarming discovery, especially when you consider that the technology has been around since 2009.
One of these vulnerabilities essentially allow attackers to “sniff on keyboard traffic”, and even inject their own keystrokes into an affected dongle. Even more frightening is that a wireless keyboard doesn’t even need to be connected to the dongle for the hack to happen. Below is just one of four other videos detailing how the flaws enable hackers to gain access to your PC.
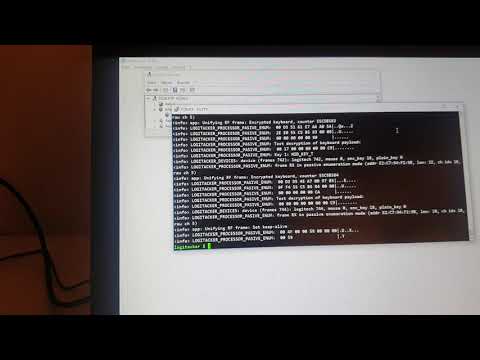
To be clear, Mengs says that the vulnerabilities affect all wireless keyboards and mice that use the Unifying USB dongles. Unfortunately, this also includes Logitech’s MX Anywhere 2S mice, which also accepts keyboard input.
Logitech, in turn, responded to Mengs’ findings, saying that it would only be releasing a patch for one of the vulnerabilities as early as August this year. However, it had no plans on releasing a firmware patch for the other vulnerabilities. If you’re interested, you can watch Mengs’ other videos on the flaws by clicking the links in the source section below.
(Source: ZDNet, YouTube [1] [2] [3])
Follow us on Instagram, Facebook, Twitter or Telegram for more updates and breaking news.



