A couple of days ago, researchers at the Dutch university, Vrije Universiteit Amsterdam (VU Amsterdam), reported the Microarchitectural Data Sampling (MDS) security vulnerability that could severely affect Intel CPUs released since 2011. Now, VU University says that Intel tried to offer the team a bribe in order to be discreet about the issue RIDL (Rogue in-flight data load)
In an interview with the Dutch publication Nieiwe Rotterdamsche Courant, the researcher said that Intel was willing to pay the researchers a “reward” of US$40000 (~RM166580) if they agreed to downplay the severity of the issue. The sweeten the pot, Intel told them that it would offer another US$80000 (~RM333160), on top of the first offer. Enticing as the offer was, the Dutch researchers refused them politely and went ahead an posted their findings.
As previously reported, the security vulnerability is caused by a flaw found inside feature known as speculation execution. As explained by VU Amsterdam, the attacker could extract sensitive data such as browser history, password, and encryption keys.
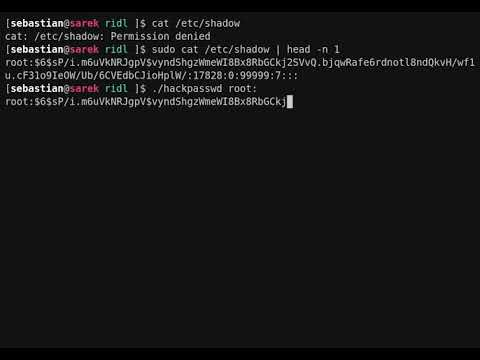
Further, had the researchers actually accepted the offer, they would’ve automatically entered an NDA with Intel, whereby they would’ve been unable to disclose their findings to anyone besides members within Intel. “If it were up to Intel, they would have wanted to wait another six months,” said one of the researchers.
(Source: Reddit via TechPowerUp)
Follow us on Instagram, Facebook, Twitter or Telegram for more updates and breaking news.



