The address bar is something that is commonly relied on as a feature used to visit intended sites. A developer has demonstrated that websites can replicate Chrome for Android’s address bar and Tabs UI, masking their true identity. Doing this allows phishing sites to disguise themselves as a legitimate site and proceed to steal sensitive information.
In his blog, Jim Fisher demonstrated just how the fake address bar shows up. As you scroll down on a web page, the address bar typically fades away to make space for the page’s content. When this happens, the fake address bar shows up, and fools users into thinking it’s the real, trustworthy thing.
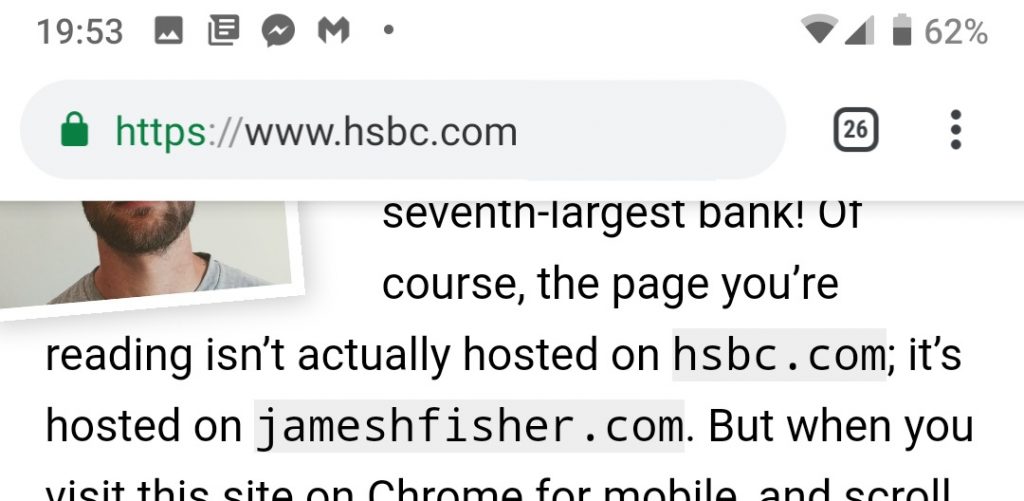
The fake site employing this can also trick the browser to never display the real address bar. Even when you try scrolling to the top of the page, a padding can be added so that you’ll never hit the very top, and the page scrolls you back down to where the content started.
Fisher says that all he did for his proof-of-concept is taking a screenshot of the Chrome address bar. He adds that, with more work, the phishing site can detect which browser is being used so that the fake address bar mimics the UI of the real thing.
9to5Google reports that one way you can check if you’re seeing the real address bar is to lock your phone and unlock it again. We tested this, and can verify that doing this forces the actual address bar to show, in addition to the fake one which will stay below it. It’s a countermeasure that works in this instance, or when you actively suspecting that something is wrong.
Either way, it pays to be more careful whenever you’re surfing the web while using Chrome for Android. You can check Fisher’s blog while using Chrome in order to experience the act yourself, though we can’t think of a reason that you would want to.
(Source: James Fisher via 9to5Google)
Follow us on Instagram, Facebook, Twitter or Telegram for more updates and breaking news.



