AMD has officially acknowledged the security flaws of its AMD Secure Processor that were revealed by CTS Labs, a digital security company that informed AMD about the flaws. The company is actively addressing the issue, and will roll out patches in the coming weeks.
AMD further stated that “these issues are associated with the firmware managing the embedded security control processor in some of our products (AMD Secure Processor) and the chipset used in some socket AM4 and socket TR4 desktop platforms supporting AMD processors.”
To bring our readers up to date; the company known as CTS Labs popped up on the internet at the beginning of last week. It created a site, amdflaws.com, along with a very brief video that briefly presented the company’s findings. The company became the talk of the (digital) town when it decidedly told AMD of its findings, just 24 hours before they made it all public.

The so-called digital security firm had supposedly warned AMD about 13 major security flaws that were spread out across four vulnerabilities. These vulnerabilities were Ryzenfall, Fallout, Masterkey, and Chimera. AMD has made it very clear that these identified security flaws “are not related to the AMD Zen CPU architecture or the Google Project Zero exploits” that were made public by the search engine giant on 3 January 2018.
The issue with both Ryzenfall and Fallout are that the flaws under these two vulnerabilities would only work if the attacker has already broken the security layer of the AMD Secure Processor, which is physically embedded in most AMD processors. Breaking through the security barriers would mean that the attackers would be able exploit vulnerabilities between the x86 platforms and PSP, installing malware that is difficult to detect.
At this stage, Ryzenfall seems to only target Ryzen, Ryzen Pro, and Ryzen Mobile processors, while the Fallout vulnerability seems to only affect AMD’s EPYC workstation CPUs.
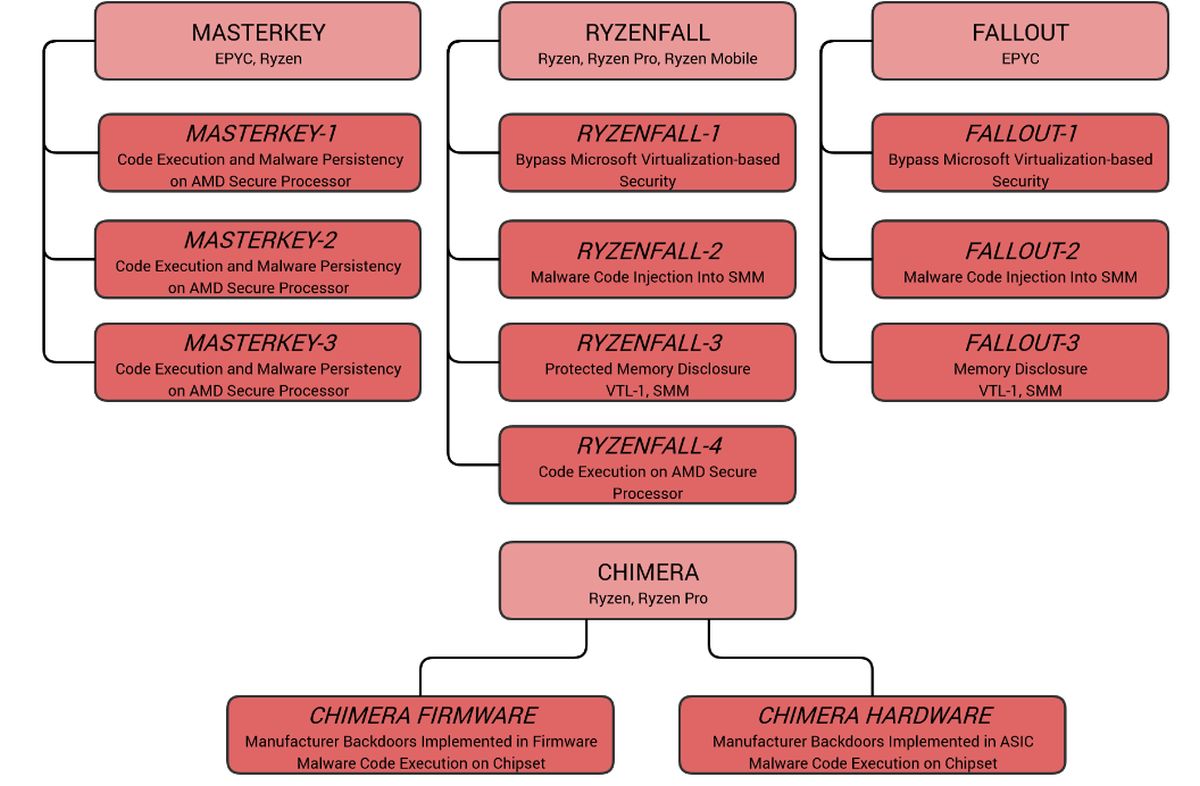
In the case of the Masterkey flaw, the purported cybersecurity firm said hackers could easily compromise a system if someone were to flash the system’s BIOS with a third-party update. This act would essentially give hackers the ability to circumvent a platform’s security controls, and even worse; the circumvention would still remain, even if one were to reboot the entire system. Masterkey also seems to only target AMD’s EPYC and Ryzen PSPs.
Last on the list is Chimera. This vulnerability targets some of AMD’s “Promontory” chipsets, which are used in its AM4 desktops and enthusiast-level TR4 Threadripper platforms. Hackers exploiting Chimera could technically access the target system via the physical memory, and then proceed to install malware that would be deemed extremely difficult to detect.
Despite the appearance of these four vulnerabilities, AMD does have some good news about all this. Firstly, all four vulnerabilities (and the hacker’s ability to exploit them) only seem possible if the hacker has administrative access to the system. On that note, AMD’s Mark Papermaster wrote that the company was already working on firmware patches that would be released as a BIOS update. Papermaster also said that these patches will be rolled out over the coming weeks, addressing each vulnerability and its corresponding flaws.
Having said all this, it should be pointed out that these vulnerabilities are not as critical as the more recent Spectre and Meltdown flaws. As written on the Trail of Bits blog:
“These types of vulnerabilities should not surprise any security researchers; similar flaws have been found in other embedded systems that have attempted to implement security features. They are the result of simple programming flaws, unclear security boundaries, and insufficient security testing. In contrast, the recent Meltdown and Spectre flaws required previously unknown techniques and novel research advances to discover and exploit.”
As far as the general consumer is concerned, what we can say is that there’s no reason to panic. Again, AMD had stated that the hacker would “require administrative access to the system, a type of access that effectively grants the user unrestricted access to the system and the right to delete, create or modify any of the folders or files on the computer, as well as change any settings.”
To put it simply; you’re not at risk, so long as you didn’t install any third-party software that could compromise the security of your AMD-based system or provide your administrative details to a technician of questionable character.
(Source: AMD, Trail Of Bits)
Follow us on Instagram, Facebook, Twitter or Telegram for more updates and breaking news.



