Data is the new currency of the realm, and the data breach that happened earlier this week in Malaysia is not going to be the last.
Let’s be frank here. Equifax, a US-based credit score rating agency earlier this month acknowledged that hackers had breached the company’s system and stole over 145.5 million customers’ information ranging from credit reports, personal identification numbers and even credit card details.
This still pales in comparison to the 3 billion Yahoo accounts and data which was compromised in 2013, or the alleged Apple iCloud breach that was allegedly involved 250 million AppleIDs.
Stop pointing fingers
There is no use pointing fingers, or finding someone to blame. It’s a useless exercise as in this day and age, data is handled and transacted by just too many people that lapses are bound to happen. The MCMC (Malaysian Communications And Multimedia Commission) can’t be making sure that every bit of data collected is secure, and neither can the recently-passed PDPA (Personal Data Protection Act) meant to block the collection of legitimate data be absolutely foolproof.
Companies who are in charge of storing mass amounts of data needs to take a hard look at their security practices to safeguard their data. As long as there is a market, there will always be people who are willing to pay for huge amounts of personal data, and as long as there are people willing to pay, there will be somebody somewhere who will be willing to take a risk and sell it.
The rise of digital crypto-currencies like Bitcoin which provides a means of transaction with very little digital trail is just going to facilitate the sale of these illegally obtained data even more.
In the case of the Malaysian data breach, The MCMC, the PDRM, and other relevant authorities are investigating the source of the breach. Even if they are able to find a source, there is just no way of knowing how much of the data has already landed in the wrong hands. And this might not be the last time it will happen.
Source of Breach
Companies that are alerted of a data breach should immediately conduct a forensic audit to see how much of their systems have been breached. In the case of Equifax, a proper forensic audit was done and the information was made public.
They also set up a dedicated site to ensure that their customers were able to check if their information was involved in the breach, and what preventive measures they should take to avoid any misuse of their personal data.
Public Awareness
If and when a data breach has taken place, each and every one who has had their data exposed needs to be alerted as soon as possible. Banks and financial institutions also need to be alerted on the individuals whose data has been compromised. Otherwise, the people who have got hold of this personal information will be able to fake documents and details, and use it to apply for everything from personal loans to credit cards without raising an eyebrow.
Identity theft also becomes a very real issue if enough of your personal information is exposed. If you are a victim of a data breach, make sure that you monitor your credit card and bank accounts for any suspicious transactions or activity.
Cloned Sim Cards
In the case of the Malaysian breach, we noted that data from some telecommunication companies were also being sold. The data didn’t just include phone numbers, and personal details of the user – it also included unique International Mobile Subscriber Identity (IMSI), unique International Mobile Equipment Identity (IMEI) numbers as well as SIM card numbers.
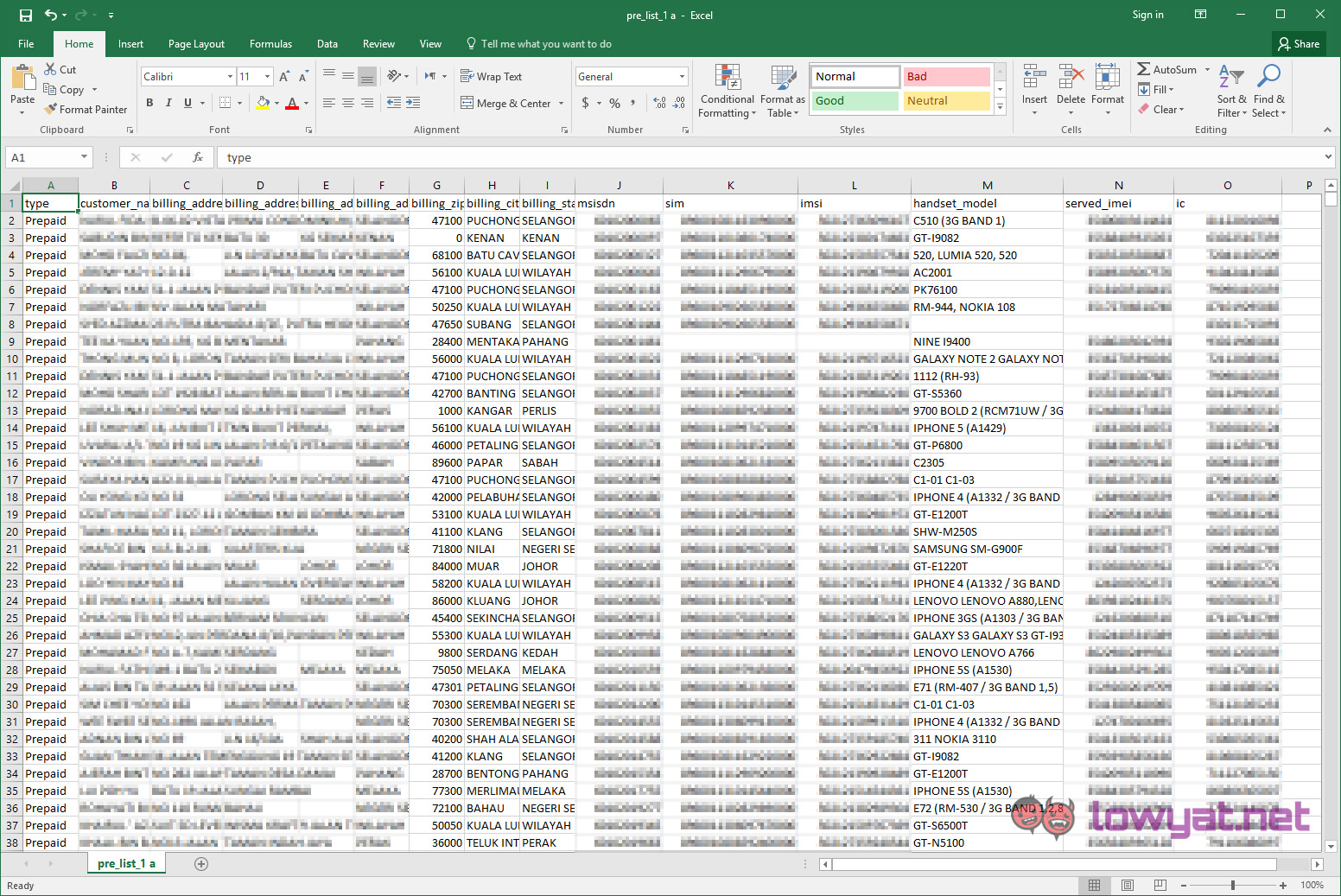
This wealth of information makes it highly possible for SIM cards to be cloned. If you notice any suspicious activity on your phone, or you receive unexplained text messages or phone calls, immediately contact your banks to alert them to temporarily freeze your account, as well as your telecommunications provider to get a replacement sim card.
Vigilance
Last week, in lieu of October being the Cyber Security Awareness Month, we highlighted the increase in spoofed calls from banks which are virtually impossible to differentiate from an authentic call. Be extra vary of any incoming phone calls, and as much as possible do not disclose any information to the other party. Whenever possible, walk to the bank or any other institution that supposedly made the call to verify whether they did indeed try to contact you.
Armed with detailed information, unscrupulous individuals will resort to social engineering (nothing to do with social media), to psychologically manipulate you to reveal information, or conduct transactions that you would not normally do. Always double check the identity of the caller, and be extra vigilant when you receive suspicious calls from people you don’t know.
No one person, or agency can be tasked with protecting personal and private data. Everybody needs to come together to ensure that when a data breach happens, the public at large is immediately notified, and remedial action is taken before the data is abused.
As we complete this article, another massive data breach involving 30 million citizens has been discovered in South Africa.
Extra vigilance, and public awareness is the two best defenses we have right now.
Welcome to the age of high-profile data breaches.


