Command and control servers are often the weak point for malware. Which is why hiding them is rather important. For a group of Russian hackers, this involves hiding commands and instructions in Instagram comments.
Security group ESET published a report on the Turla group’s watering hole campaign, where this technique was first noticed. The idea is that the Turla malware targeted government officials and agencies with a compromised Firefox plugin. The plugin uses a bit.ly link to look for its C&C server, but the link is no hardcoded into the malware itself.
Instead, it is directed to a particular post on Instagram; in this case a specific photo posted by Britney Spears. The malware scans the comments and turns them into hash values; and it’s looking for a specific value in mind. The comment itself resembles any other badly written Instagram post, but also contains hidden characters that help add up to the required hash value.
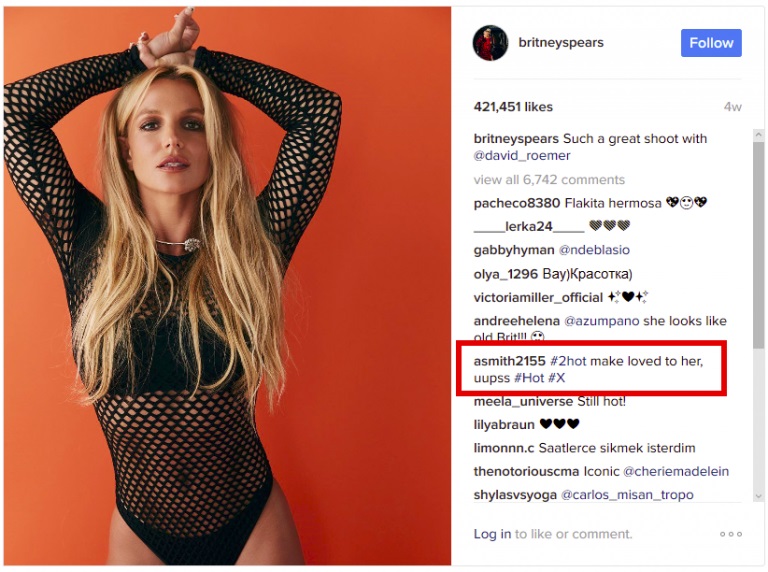
Running the hash through regex returns a specific bit.ly link; which contains the address for the actual C&C server.
This creative use of social media aside, the malware aside is a relatively standard backdoor. It’s capable of executing files, uploading and downloading files to the C&C server, and read directory contents. Mostly, it looks to be a module for spying on foreign governments.
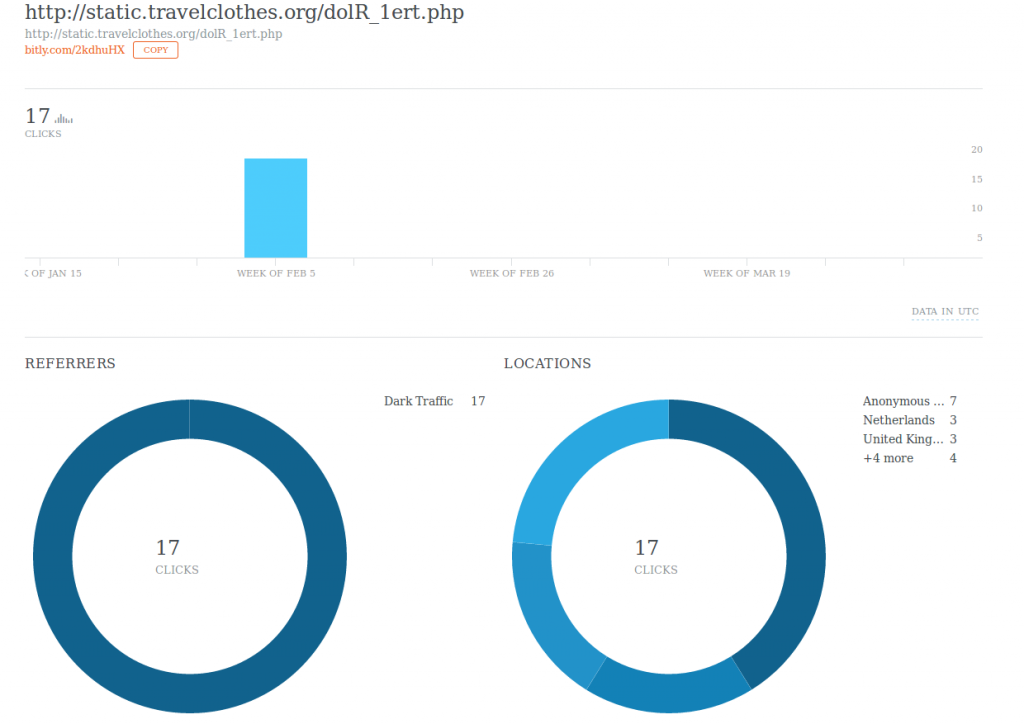
Hiding comments in social media makes it more difficult for security programmes to detect suspicious traffic. Since people are more than likely to be accessing those sites on their own, allowing the malware to hide its activity more efficiently. It also allows the hackers to change the C&C server more easily, since all they have to do is tell the malware what hash value to look for.
[Source: ESET]
Follow us on Instagram, Facebook, Twitter or Telegram for more updates and breaking news.