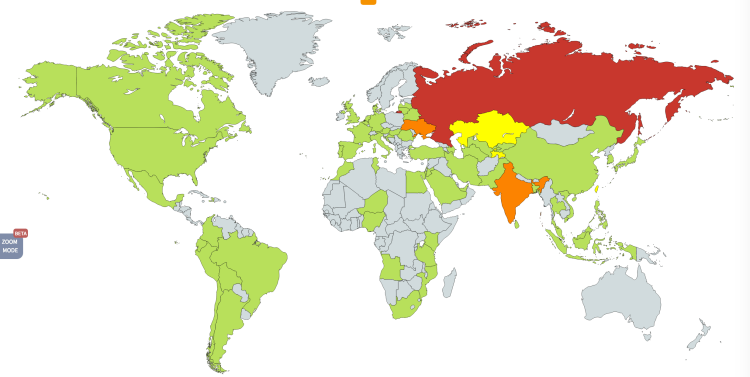
It turns out that the massive ransomware attack that happened last week did not affect as many Windows XP machines as first believed. Statistics from Kaspersky Lab are showing a disproportional number of Windows 7 computers falling victim to the malware; with Windows XP making up an insignificant number.
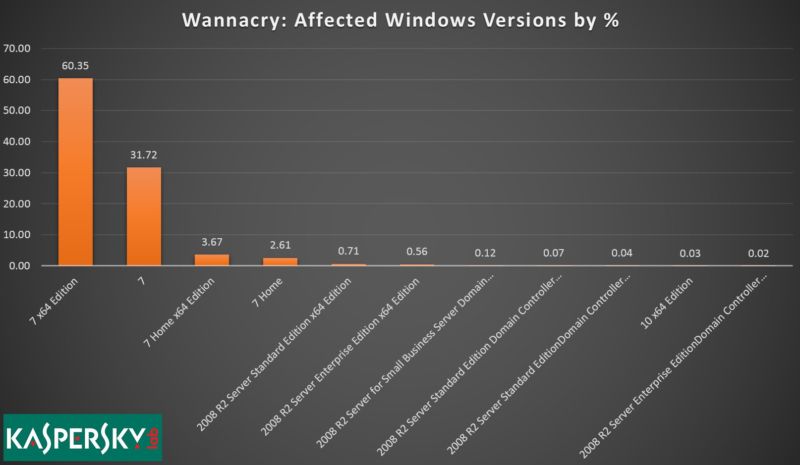
According to the report, 97 percent of all infected computers were running on some version of Windows 7. The second most affected operating system was Windows R2 Server 2008, with all versions making up 1.6 percent of the infected machines. Windows XP had so few recorded infections that the security company didn’t even bother including it on the chart.
https://twitter.com/craiu/status/865562842149392384
This data raises an interesting point about security patches. Microsoft still supports Windows 7 with weekly updates; meaning that the SMB vulnerability should have been patched. Especially since the developers were well aware of its existence. People just weren’t installing the security patches like they are supposed to.
One further observation is that 64 percent of the infected computers were running Windows 7 x64 Edition, which is primarily used by businesses. Indicating that it is corporations who are the least concerned with installing security patches, despite having the most to lose in an attack.
Further information about Wannacry’s attack vector has also surfaced. Researchers believe that spam email and phishing attacks were not the primary source of infection. Instead, the attackers simply scanned for computers with open SMB ports and used those to gain access to systems. Once inside a computer, it exploited the same vulnerability to spread access the entire local network.
This would have explained how the ransomware propagated so quickly, since it didn’t rely on people having to check their email and click on an attachment.
The Wannacry attack is over at the moment, but there is evidence that hackers are trying to resurrect it. A copycat version of the malware was said to be spreading shortly after the first outbreak was stopped. However, the knockoff version still had the killswitch hardcoded into it and turned out to be a dud.
For now, the best course of action would be to update all computers with the latest security patches. The patch should close off the exploit and immunise the computer from any further attacks using the SMB vulnerability. That’s not to say that there aren’t any other exploits the NSA hasn’t been hoarding from the world.
[Source: Ars Technica]