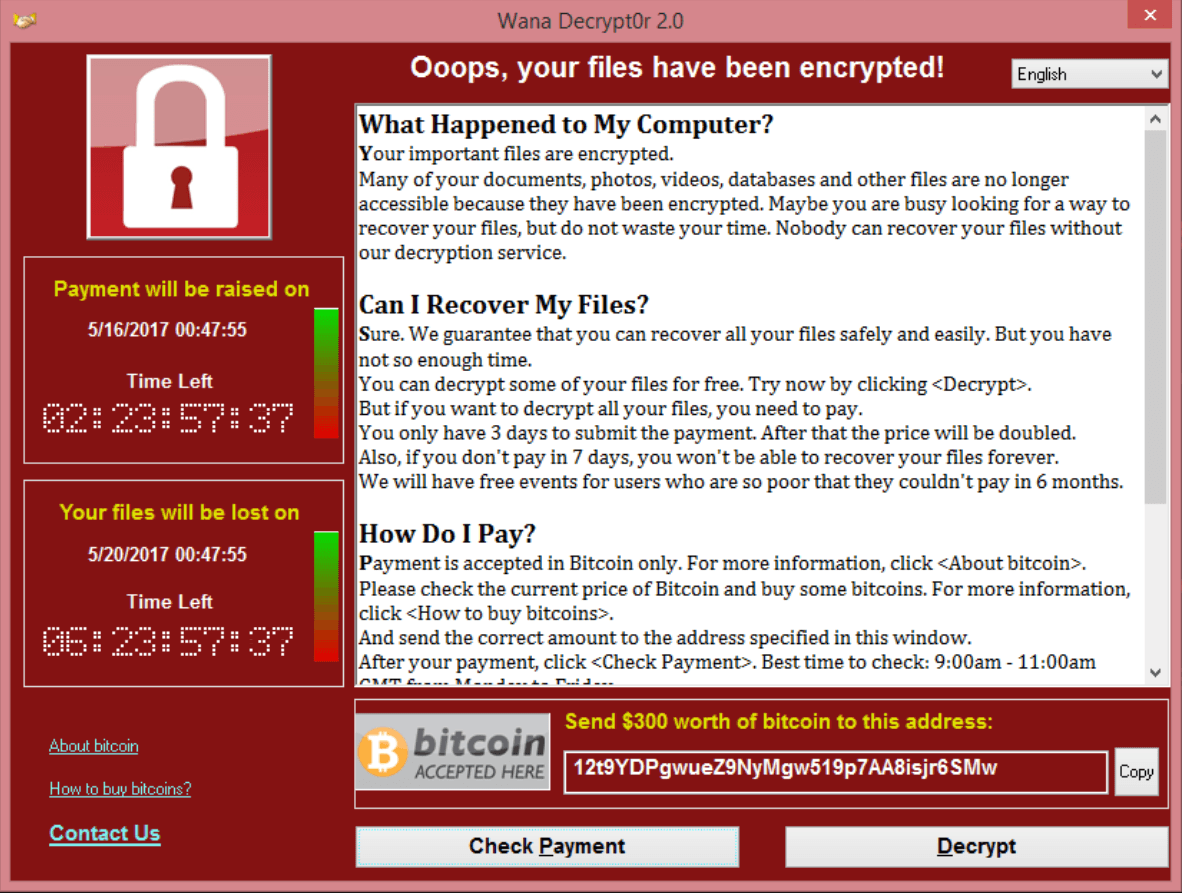
A massive wave of ransomware held the world hostage over the weekend. Wcry, the particularly devastating piece of malware, was designed to use National Security Agency exploits leaked last month. In all, it spread to over 100 countries; although there are conflicting reports on whether Malaysia was affected by the mass attack.
Wcry targets an exploit with the SMBv1 file sharing system on Windows machines to spread across networks. For the most part, home systems are safe as Microsoft patched the exploit a month before it was leaked. However, the security patches were released for versions of Windows that are still supported; which left out anything still running on anything earlier than Windows XP and Windows Server 2008.

Still, Microsoft rushed out patches for all affected operating systems, even if they are no longer supported (Windows Vista and earlier). This makes for the unusual situation of end-of-life products receiving support; but the threat of Wcry has motivated the company to take extreme measures.
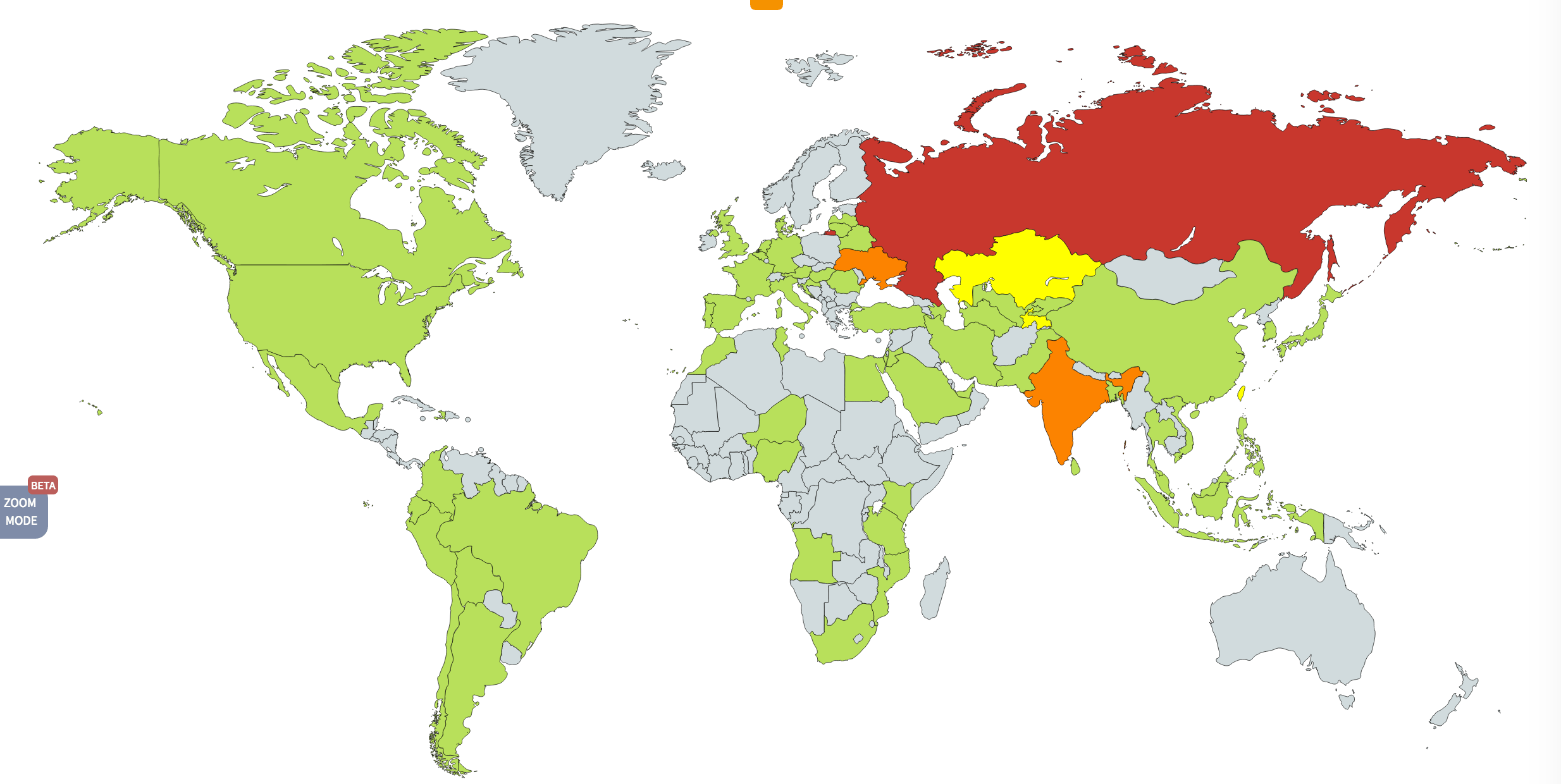
For the most part, this affected large institutions that haven’t migrated to more modern operating systems. The UK reported that some 70 hospitals that form part of its National Health Service began turning away patients after, while employees of Spanish telecommunications giant Telefonica were ordered to shut down their work computers to stop the spread of the virus.
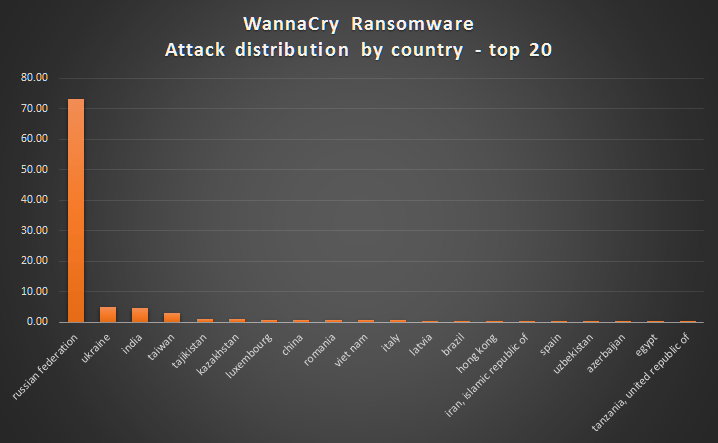
Russia was disproportionately the target of the attack for some reason. With the country reporting more than 10 times as many infections as any other country.
Whether Malaysia was among the victims is currently unclear. On Sunday, the Malaysia Communications and Multimedia Commission issued a statement saying that there were no reports of Wcry in the country. However, The Star has reported that Cybersecurity Malaysia has received reports of infections.
The cybercriminals were asking for a modest sum on every computer infected, although it appears that they had increased the amount as the malware spread. Systems that were infected early in the attack were asked to pay $300 in Bitcoin, while later noticed raised this to $600.
For the most part, the spread of Wcry has been halted by a researcher who accidentally triggered the ‘kill switch’. Going by the pseudonym MalwareTech, he bought a web address that the malware was reporting to in order to discover its origin. This has the unexpected effect of stopping the malware from continuing to propagate.
There were later reports that a new version of Wcry without the kill switch had appeared in the wild, but these are unverified. No official reports of new infections have appeared since.
The threat is gone for now, but future cybercriminals will very likely look to this attack as a success. There is a reason that companies like Microsoft are forcing security updates on users these days, and this happens to be it. Although, it situation is not nearly as simple for large corporations which are built on legacy technologies.
[Source: Securelist, Symantec, BBC]
Follow us on Instagram, Facebook, Twitter or Telegram for more updates and breaking news.