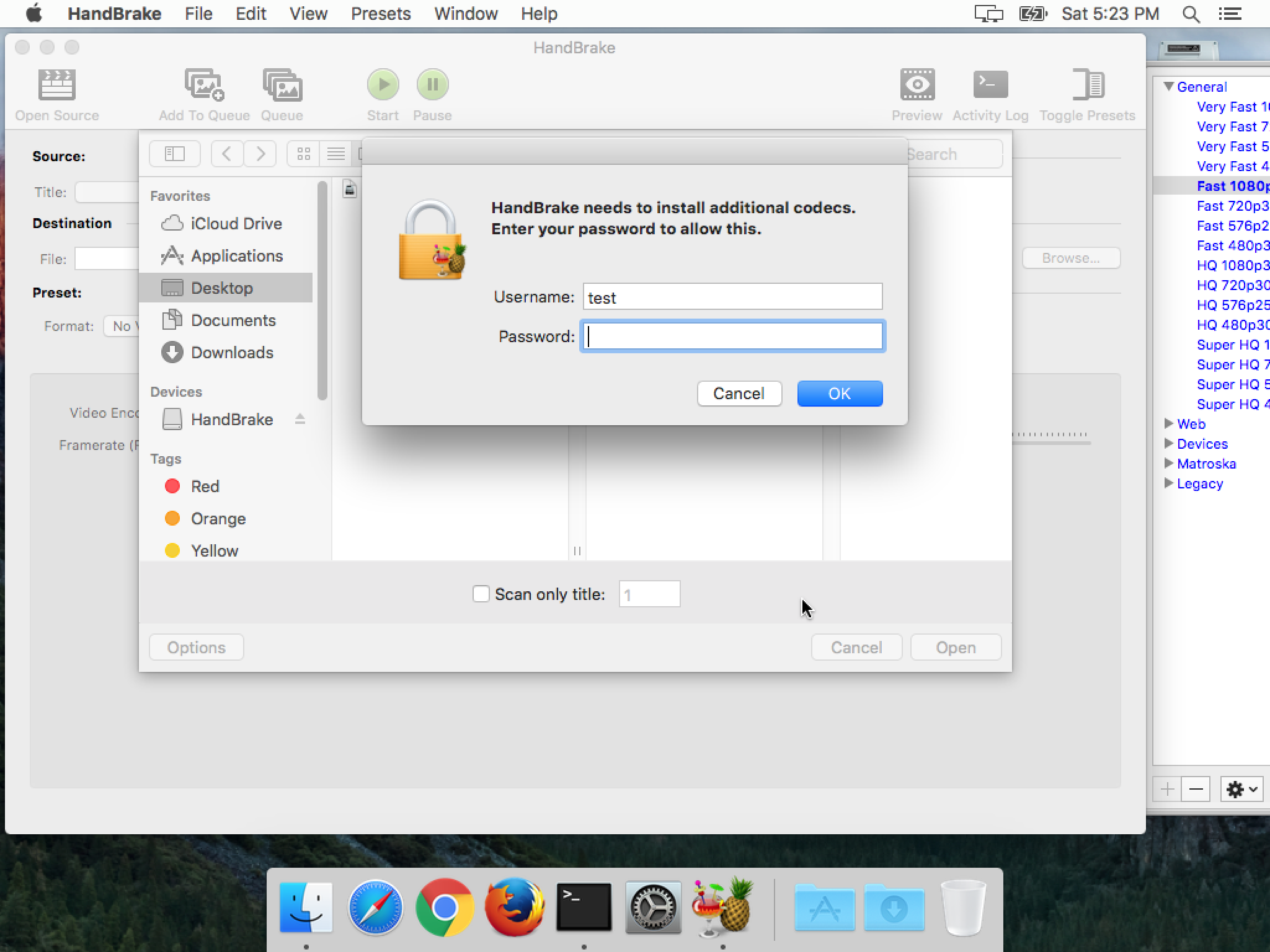
Malware targeting OSX is really coming into its own in 2017. Handbrake, a popular open source video transcoder, was hacked and replaced with a version that steals passwords.
One of the two download servers for Handbrake became compromised, which makes it much more difficult for Mac users to determine if they fell prey to the attack. Those that did should have seen a dialogue box asking them to enter an admin password. This doesn’t actually log the user in to anything, and is a phishing attempt.
The malware then exfiltrates browser data, keychains, and 1Password data. Naturally, the admin password stolen earlier is then used to decrypt the information in the keychains and access the passwords stored in 1Password.
Worried users can check the SHA1 hash of the file by typing “shasum path/to/HandBrake-1.0.7.dmg” in the terminal. The “path/to” section should be the directory in which Handbrake is stored. If the hash is “0935a43ca90c6c419a49e4f8f1d75e68cd70b274” then the file is compromised and should be deleted.
Of course, this also means that the user will have to change all his or her passwords. Just to be secure all the other accounts.
Malwarebytes notes that this version of the Proton malware has been on sale on the DarkWeb since earlier this year. It costs an impressive 40 BTC (about RM256,000) to purchase for multiple uses; although there’s the budget option for 2 BTC (about RM14,800) per installation.
If anything, the person behind the malware is making a killing from just selling this to less technically skilled hackers.
[Source: Malwarebytes]
Follow us on Instagram, Facebook, Twitter or Telegram for more updates and breaking news.