A phishing scam using an elaborate facsimile of Google Docs has been shut down. The campaign sent out emails claiming to be a contact sharing a Google Docs link, but instead took control of the victim’s account and sent more copies of itself out.
According to Ars Technica, the attack seems to have originally targeted reporters; but has since spiraled out of control. The email itself uses a technique attributed to Russian intelligence services. This involves using the OAuth authentication interface to request permissions from the intended victim.
The latest attack copied the Google Docs OAuth interface down to the wording used by Google. In fact, the only clues that this was a phishing attempt were extremely subtle and could easily be missed by just about anyone. That said, there were giveaways that indicated something wrong.
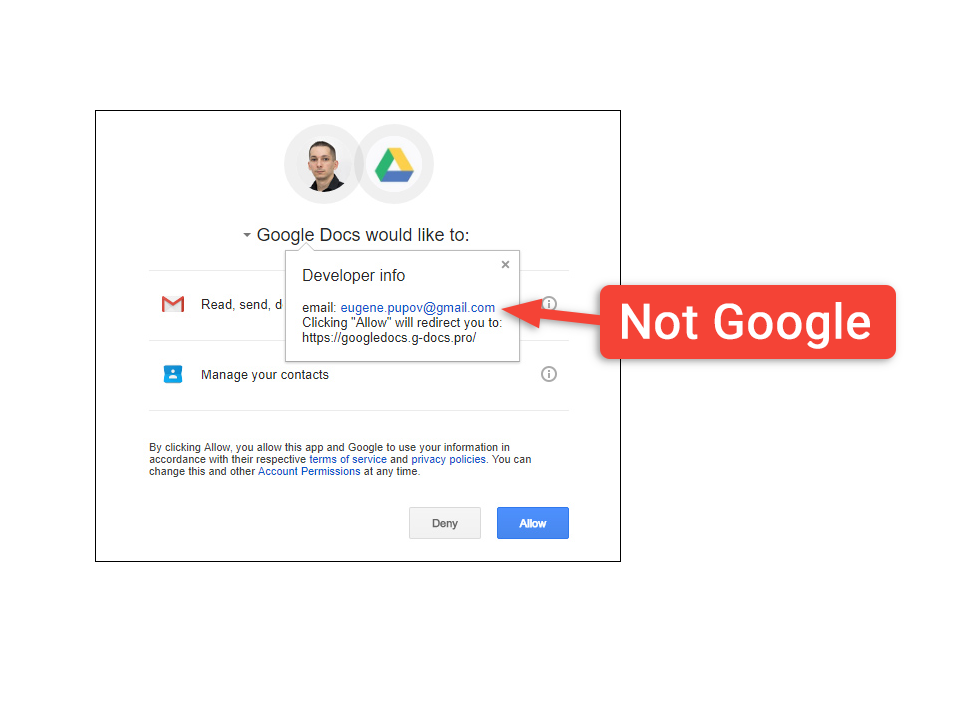
For instance, the recipient’s email address appears in the BCC line and not the regular ‘To’ space. Also, the OAuth interface lists the developer of the app requesting permissions as being something other than Google. However, the developer information happens to be hidden from view.
It’s unknown what the attack aimed to achieve. On the surface, it looks like a simple phishing attempt to gain access to email information. Then again, the similarities to a state sponsored actor may indicate that something else is going on.
In any case, Google has already deleted the sites associated with the attack and removed all permissions from the affected accounts. A move that was rather simple as the attack vector was closely tied to Google’s own services. Still, we expect the company to examine its current services to prevent this sort of thing from happening again.
[Source: Ars Technica]
Follow us on Instagram, Facebook, Twitter or Telegram for more updates and breaking news.


