Android phones running on MediaTek processors have been found with a backdoor bug that leaves them vulnerable to attackers. The problem lies with a debug feature that was included to allow for telecommunications inter-operability testing. This feature is normally disabled before the phones are shipped; only, it turns out that manufacturers didn’t turn it off and have now exposed customers to possible rootkit attacks.
MediaTek has declined to reveal which manufacturers skipped this important part of securing smartphones before shipping them. However, the vulnerability only known to affect the MediaTek MT6582 chipset at the moment; although it is unknown how many other processors are actually affected.
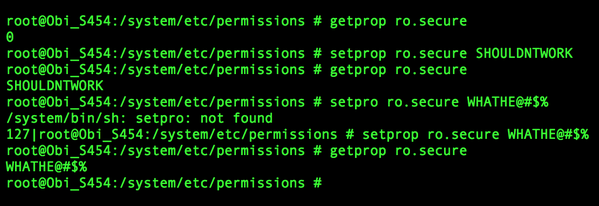
Security researcher Justin Case, who first discovered the problem, noted that read-only properties should not be changed after booting the device. In this case, the problem is that MediaTek made it so that the properties can be changed by just about anyone. This in turn could allow attackers to gain root access to the device and pretty much do anything they want to it.
While MediaTek is aware of the problem, there is little it can do to close the backdoor. The company has already contacted the affected manufacturers and asked them to be more careful, but there is no word on coming up with a fix for the devices that have already been sold.
On the bright side, there aren’t that many devices running on the MediaTek MT6582; and most of these are lower end devices. Essentially, this won’t cause a massive data leak (yet); but it could possibly come back to bite MediaTek and its partners at some point in the future.
[Source: Gadgets 360, Justin Case (Twitter)]
Follow us on Instagram, Facebook, Twitter or Telegram for more updates and breaking news.


