The hacker behind the cyberattack on the San Francisco Municipal Transportation Authority has received a taste of his own medicine. It turns out that the ransom note left on computer terminals lead a security researcher to his inbox; which was promptly compromised and password changed.
The Muni operates the public transportation network in San Francisco, and was left unable to collect payments or electronically assign routes after the attack. Payment kiosks could only display a ransom note directing the SFMTA to contact the hacker in order to arrange for payment. In contrast to earlier reports, the SFMTA has said that it never considered paying the ransom; despite having to provide free rides to passengers for several days.
 As karma is relatively unfriendly to most people, the contact information turned out to be all that was needed for a lone researcher to track his location. It turned out that the Muni hacker failed to properly secure the account, and had his password guessed rather quickly. From there, the researcher took control of the account and turned over his findings to security blog KrebsonSecurity.
As karma is relatively unfriendly to most people, the contact information turned out to be all that was needed for a lone researcher to track his location. It turned out that the Muni hacker failed to properly secure the account, and had his password guessed rather quickly. From there, the researcher took control of the account and turned over his findings to security blog KrebsonSecurity.
Login information for the email server revealed that the owner was likely accessing it from a location in Iran. That being said, it was also tied to a Russian phone number; which indicates that the owner was at least trying to conceal his identity. Despite the phone number, the researcher believes that the hacker is of Iranian origin. Largely due to several notes being written in what appears to be Farsi.
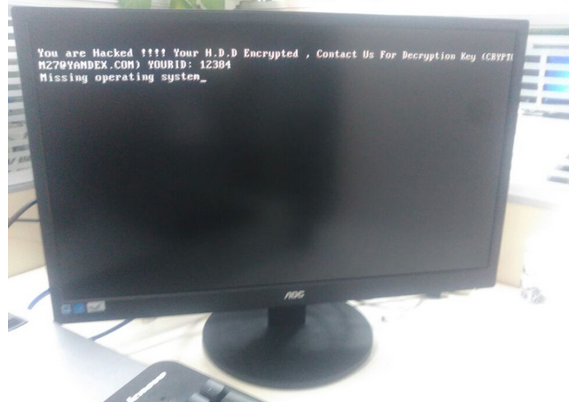
The counter-hack also revealed that the mysterious Muni hacker had previously targeted smaller construction companies; and had extorted around 1 Bitcoin per compromised server. Emails revealed that he had successfully collected 63 BTC (worth about RM205,500) from American firms.
It’s uncertain if the Muni was deliberately targeted or was simply an unwitting victim of a wider ransomware campaign. Although, it turns out that the hacker had also offered to provide advice on how to prevent future malware attacks to his victims for additional payment. Surprisingly, this ploy worked on occasion; with the criminal being paid twice for his efforts.
[Source: KrebsOnSecurity]
Follow us on Instagram, Facebook, Twitter or Telegram for more updates and breaking news.



