A critical flaw has been discovered in Linux’s Grand Unified Bootloader (Grub). The bootloader has a password feature to prevent unauthorised access to boot entries, mainly to secure it against tampering but can also be used to seal off parts of the OS. However, a bug in the programming allows just about anyone to bypass the password by hitting the backspace key.
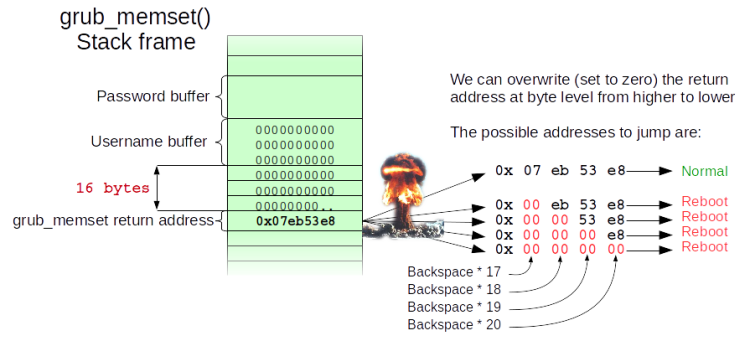
The flaw was discovered earlier this month by Hector Marco and Ismael Ripoll from the Cybersecurity Group at Universitat Politècnica de València. In practice, all the user has to do is hit backspace 28 times in the user name field; which in turn will either cause the system to reboot or launch into the Grub rescue shell. The important bit is to get into the rescue shell, which provides unrestricted administrator access to the entire system. From there, the attacker can rewrite the Grub code to bypass the password requirement.
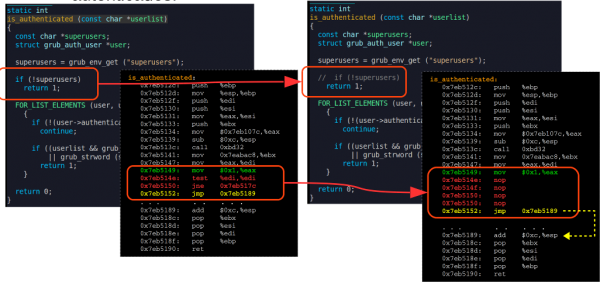
What happens is apparently an integer overflow problem. It turns out that hitting backspace is deleting characters that do not exist, which triggers an exception to the authentication protocols. Which why the rescue shell launches to allow the user to fix the problem.
Naturally, this only matters if the attacker has physical access to the computer. It doesn’t appear to work over internet connections, but there are ways of getting in front of the computer that needs to be hacked.
At the moment, the issue affects all Linux distros. Thankfully, they have released fixes for the vulnerability and Linux users should ensure that they have their systems patched.
[Source: hmarco.org, PCworld]