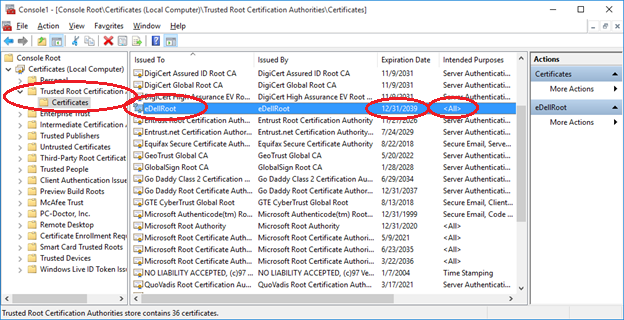
The Lenovo Superfish debacle showed us why pre-installing self signed Root Certificates on laptops is a terrible idea. Unfortunately, it looks like Dell has not learnt from the revelation as several Dell users have discovered that the company has been making the same mistake.
Unlike Superfish, the purpose of Dell’s self signed Root Certificate is entirely unclear. It does not appear to do anything in particular. However, like Superfish, it represents a potential security flaw that can be exploited by malicious hackers.
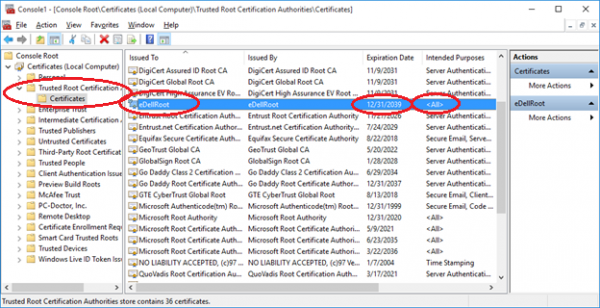
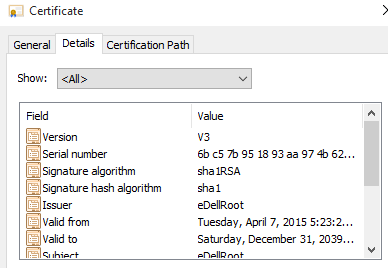
The problem happens to be that Dell’s eDellRoot certificates are all signed with the same private key; which happens to be stored on the computer. The danger here is that extracting the key is not entirely difficult for a dedicated hacker. Once extracted, the key can be used to spoof legitimate websites; making the fake look secure because it will be HTTPS-protected.
Tests have shown that sites faked with the eDellRoot certificate are able to fool most browsers. Google Chrome and Microsoft Edge both failed to identify a website set up with the certificate as being fraudulent; although Firefox still managed to throw up a warning.
At the moment the problem seems to appear on newer Dell machines. Particularly those sold in the last six months. It is known to be pre-installed on Dell Inspiron 5000 series and XPS 15 laptops; and is suspected to also affect Inspiron desktops, the Latitude series, and various Precision M4800 models.
Dell is currently looking into the problem, but has not commented on why the certificate was installed in the first place. Of course, the logical conclusion is that the company was trying to do the same thing that Lenovo was when it got caught. However, since no ads have been served using the certificate, it really is anyone’s guess as to what Dell is actually up to; besides exposing customers to security threats.
Update: Dell has pointed us to an official statement made about the issue. Turns out that the certificate was simply to make it easier to identify systems for tech support purposes. The company will be releasing a software update today that will remove the certificate from affected systems.
[Source: Reddit, Ars Technica]