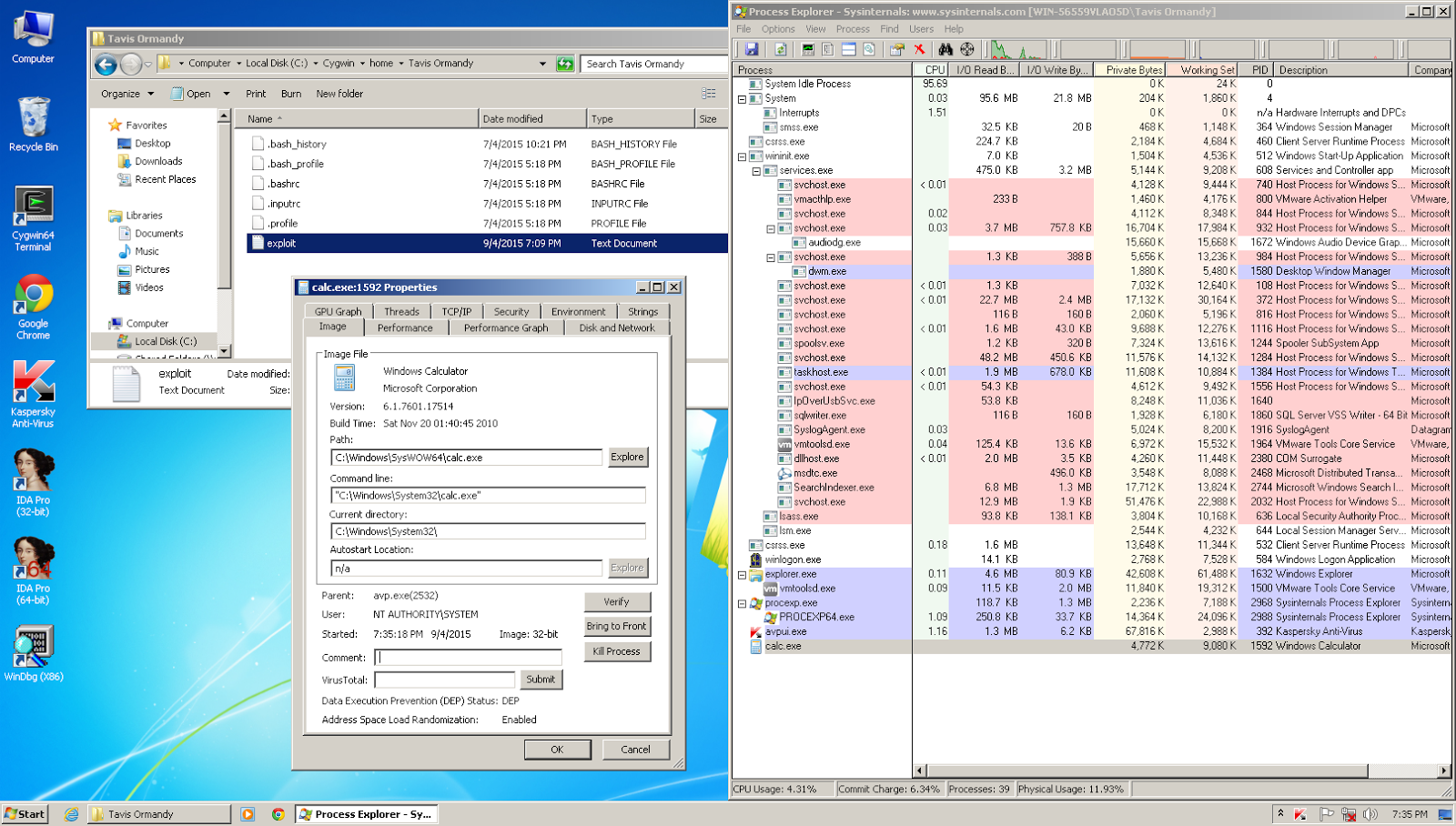
Security software exists with the intention of protecting computers from attackers and malware. However, research is showing that these antivirus programmes are not as secure as people believe they are, and could potentially open people to attacks that they would otherwise be safe from.
Tavis Ormandy, a researcher with Google’s Project Zero team, found a number of bugs in popular antivirus programmes that could be used to remotely execute malware. He also pointed out that there is an active black market for these kinds of exploits, and attackers pay good money to learn of the vulnerabilities. One such company that exploited these weaknesses was spyware vendor Hacking Team, who was itself recently hacked.
Ormandy’s most recent blog post about the matter highlights a number of vulnerabilities with Kasperksy Lab, which he says could be exploited in highly targeted attacks. Ideally, this means that the average user is not in danger of having this sort of vulnerability used against him; and that the attackers would likely be state sponsored with access to large amounts of resources.
Kaspersky was not the only antivirus found to be lacking in its defences. Both ESET and Sophos have been discovered to have exploits that could be used against the system. Ormandy has not looked into other security software providers yet, but has promised to examine them in the future.
Fortunately for Kaspersky users, the company has responded quickly to Ormandy’s revelations and is in the processor of making architectural changes to its products to better resist exploits.
While Kaspersky, and presumably other antivirus vendors, are taking the threats seriously, it is an unsettling thought to know that our computer defences can be used as an additional attack vector. That is not to say that everyone should uninstall their antivirus, computers are still less likely to be infected by malware without the additional layer of protection. Rather, it looks like the vendors will have to pay more attention to what they are doing and be extra vigilant about any potential exploits in their work.
[Source: Google Project Zero Blog]
Follow us on Instagram, Facebook, Twitter or Telegram for more updates and breaking news.