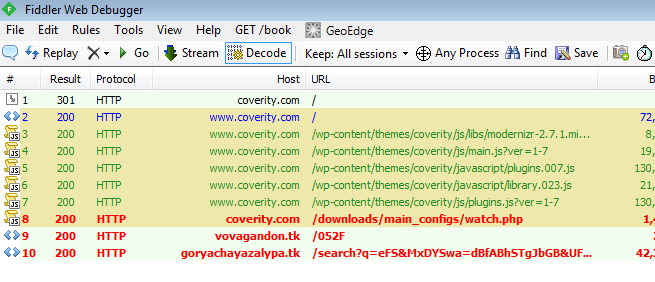
Several thousand Wordpress sites have been hijacked by attackers and have been redirecting visitors to a Nuclear Exploit Kit landing page. The malware campaign began over two weeks ago, but has recently seen a massive spike in activity.
Daniel Cid, CTO of security firm Sucuri, says that the infection rate went from 1,000 per day to more than 6,000 per day on Thursday. There has been no explanation as to where the additional activity came from, although it looks like the campaign has become active enough that 17-percent of the affected sites have been blocked by Google for suspicious activity.
![]()
Unsurprisingly, the attackers are using a Javascript exploit to force browsers to redirect visitors of the infected sites to the own landing page. Once that happens, the Nuclear Exploit Kit hurls a variety of exploits against the user in an attempt to deploy its payload.
There is no mention about what the malware is attempting to accomplish yet, but the goal of the campaign should become clear as it becomes more widespread. At the moment, Sucuri has dubbed the attack “VisitorTracker”, after one of the function names of the injected Javascript files.
No list of affected Wordpress sites has been provided, but Sucuri has provided a tool for checking if the particular site has fallen victim to the attack.
[Source: Sucuri, via Ars Technica]
Follow us on Instagram, Facebook, Twitter or Telegram for more updates and breaking news.

