Italian spyware maker Hacking Team is currently facing a massive nightmare. The company has had its security breached, and some 400GB of files leaked on to the internet. Human Rights associations and privacy advocates are having a field day sorting through the data which shows sales to numerous oppressive regimes.
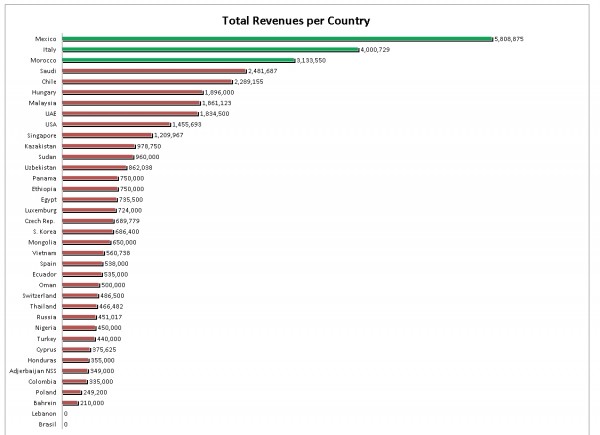
Hacking Team makes a living by selling spyware to governments and law enforcement agencies. It’s main product allows customers to remotely access infected computers to copy files, log all communications, and even activate the computer’s microphone and webcam to monitor the user. Most importantly, the company is not selective about who it sells the spyware to; with the files showing customers including countries with histories of human rights abuse like Sudan and Ethiopia.
The cyberattack also exposed numerous passwords used by Hacking Team and its customers, as well as documents about the configurations of the spyware that was bought. Interestingly, the passwords that are circulating from the data dump show just how little thought was put into them. Examples of these weak passwords include HTPassw0rd, Passw0rd!81, Passw0rd, Passw0rd!, and Pas$w0rd.
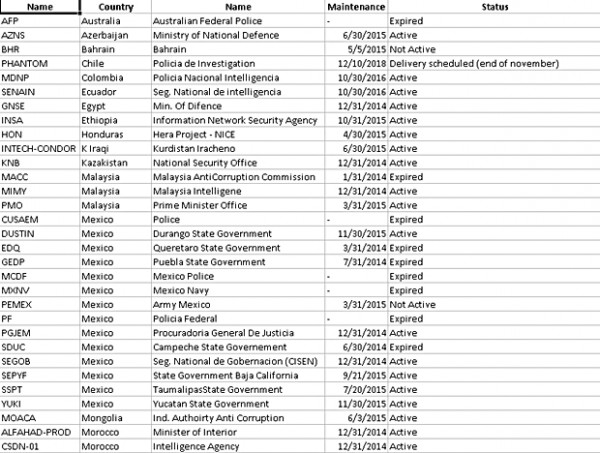
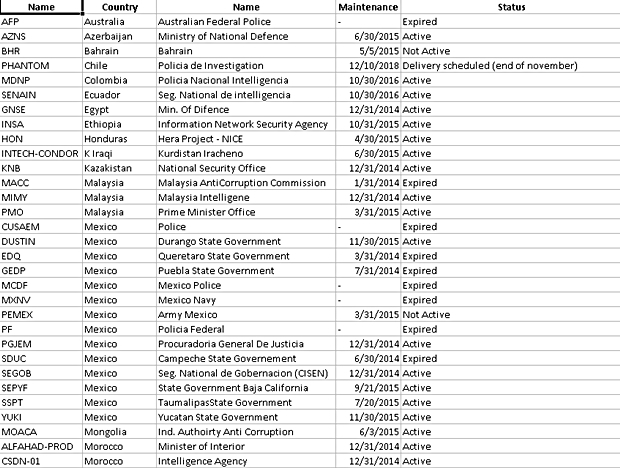
Three entries from the list of customers would be of interest to Malaysians as these list the Malaysian Anti-Corruption Commission, Malaysian Intelligence Agency, and the Prime Minister’s Office. The documents note that the MACC’s license for the spyware expired in January 2014, but the two other government bodies still have active subscriptions. There might be more details about this entry, but they have not yet surfaced as analysts have had less than 24 hours to go over the data.
[Source: CSO]
Follow us on Instagram, Facebook, Twitter or Telegram for more updates and breaking news.