
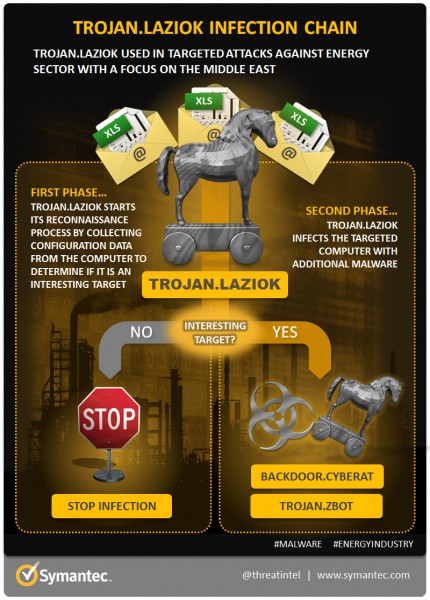
A new Trojan that targets the global energy sector has been discovered. Currently known as Laziok, it appears to mine information from targets mainly located in the Middle East, allowing its controller to customise future malware for delivery to the infected systems.
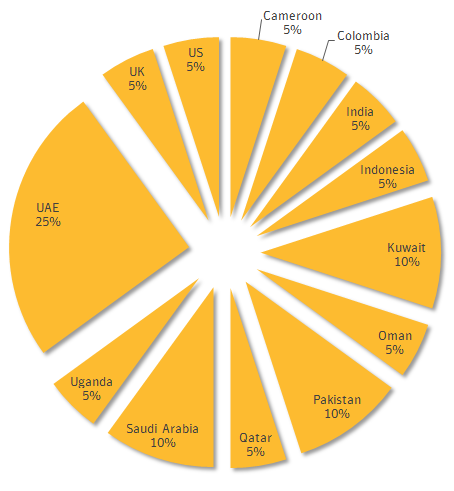
Symantec first observered Laziok in the wild infecting targets linked with pertroleum, gas, and helium industries. About a quarter of the victims were located in the United Arab Emirates, while other countries like Kuwait, Saudi Arabia, and Pakistan also had a similar number of victims.
The Trojan originates from the moneytrans[.]eu domain, and exploits an old vulnerability found in Windows systems. Microsoft has already patched this vulnerability, but it appears that the attackers are hoping to catch victims who are not up to date on security patches and are therefore less capable of defending themselves against cyber-attacks. Once the infection succeeds, Laziok sends the details of the system back to the C&C server; which results in the attackers later dropping customised versions of CyberRat and ZBot malware.
This attack appears to simply be a reconnaissance run for the attackers, who are simply content to collect information from the infected systems. Symantec notes that the attack is not very sophisticated as it uses an old exploit to distribute well known threats. The attack could easily be defeated by modern security protocols, although there is the possibility that this was simply done to test the capabilities of the oil and gas industry.
Fortunately (?), this does not look like a state sponsored attack as it lacks the sophistication seen in more complex malware that has been used by the US lead Five Eyes surveillance network. Or, it could just be more cyber-spies working with low-tech solutions to cover their tracks.
[Source: Symantec]
Follow us on Instagram, Facebook, Twitter or Telegram for more updates and breaking news.



