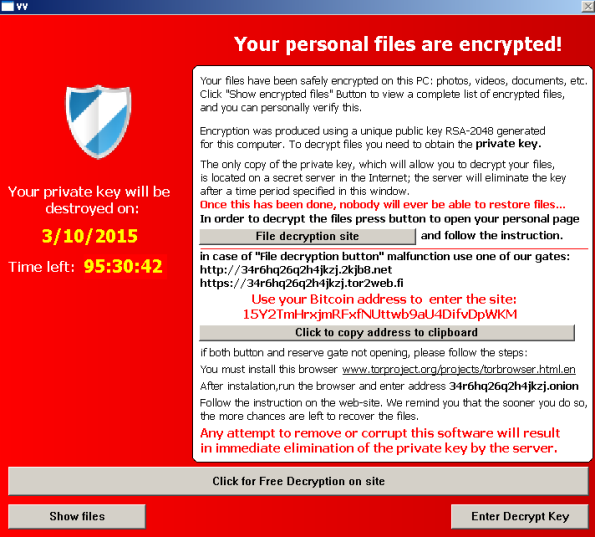
A new piece of ransomware that rides on the ideas created by CryptoLocker has been spotted in the wild. Currently known as TeslaCrypt, it encrypts specific game files to render them inaccessible to users. TeslaCrypt then demands some US$500 (about RM1847) in Bitcoin for the key to retrieve the files. This makes it the latest iteration in a growing type of malware that extorts money from users in this manner.
Ransomware is a kind of malware that locks files on a computer using a complex encryption method, essentially preventing anyone from viewing those files without the corresponding public key. Naturally, the hackers are the ones who own the key, and often offer to sell it to the victim. This form of extortion isn’t too common yet, but is apparently growing in popularity among cyber-criminals. The anonymous nature of cryptocurrency has also made it safer for them to demand payments without the risk of being tracked through banking transactions.
TeslaCrypt is unique in that it is the first ransomware that targets games specifically. Not every game is at risk, and researcher Vadim Kotov notes that around 20 titles are affected. It would appear that the cyber-criminals behind the malware are attempting to lock some of the more popular games like Starcraft 2, Minecraft, Call of Duty, League of Legends, and Dragon Age: Origins. TeslaCrypt also targets Steam itself, as well as specific files from companies like Electronic Arts and Valve. Game development tools RPGmaker, Unity3D, and Unreal Engine are similarly targeted.
The ransomware is deployed using a compromised Wordpress website that had been used to redirect users to a page with a malicious Flash exploit. The exploit mainly targets Internet Explorer and Opera browsers, and presents affected users with a link to a “hidden service” TOR site.
There is currently no way to recover the affected files, besides simply paying the ransom. This is a problem that researchers are also facing with the initial CryptoLocker attack, and it doesn’t look like anyone is getting close to cracking the 2048-bit RSA security. That being said most users should be safe if they keep their software and antivirus up to date due to the limited attack vector of TeslaCrypt.
[Source: Bromium, via Ars Technica]

