
Lenovo had a less than happy Chinese New Year as it was discovered to have installed adware that hijacks web sessions, leaving users vulnerable to HTTPS man-in-the-middle attacks. It becomes worse as the difficulty in defeating the encryption of the adware is so easy that researchers managed to guess the password in three hours.
The threat is present on Lenovo computers shipped between October and December 2014, and comes courtesy of a company called Superfish. This particular adware installs a self-signed root HTTPS certificate that intercepts encrypted traffic from the user, and also falsely represents itself as a official website certificate for HTTPS connections. Essentially, instead of checking whether the website is actually certified as the original, Superfish signs off on it itself and does not inform users.
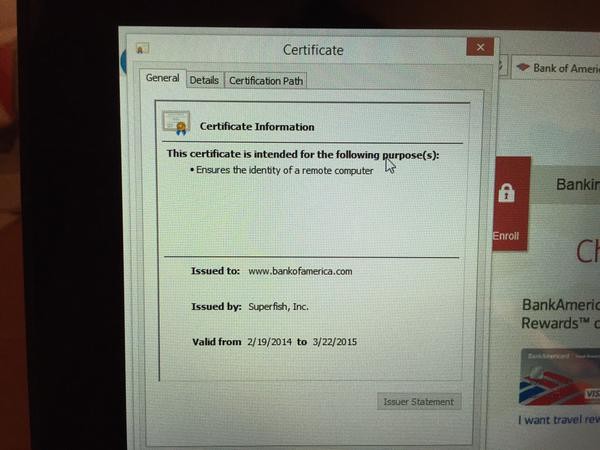
This behaviour is extremely dangerous as third parties can hijack the adware and use it to redirect unsuspecting users to their own data mining sites. To make matters worse, the root HTTPS certificate allows the redirecting to happen even with firewalls and other security precautions in place; since the computer accepts the Superfish certificate as legitimate. The measure also circumvents Google Chrome, which is set up to detect suspicious website behaviour.
Lenovo itself has shut down the Superfish servers, and no longer pre-installs it in systems as of January 2015. However, it has claimed that it thought users would like to see advertisements appearing on websites with secure connections. Superfish itself was being sold as a feature of using Lenovo computers, albeit one that was not mentioned in any marketing material or documentation.
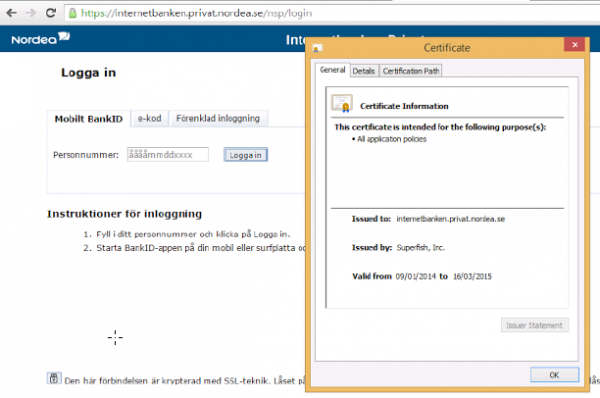
The company has released software that will remove Superfish from computers, but it is unknown how long this will take. Lenovo had originally said that the system was fully secure, and that nobody would be able to crack the 1024-bit RSA encryption. While that is true, the private key to the encryption can be extracted by using a simple password that was guessed within an afternoon.
There is a bright spot to this as Microsoft has announced that Windows Defender will remove Superfish from computers. However, there is a catch to this. Windows Defender remains turned off if the user has a different anti-virus programme installed. This was done as a concession to vendors who wanted to pre-load their own choice of anti-virus for users, most of which come from partnerships with security companies.
Windows Defender itself will only activate if the computer remains unprotected by any anti-virus for a couple of weeks. In other words, the only way to remove Superfish right now is to uninstall all security and wait for Microsoft’s built in solution to kick in.


