Kaspersky Lab has unveiled details about the most advanced cyber-espionage campaign ever detected. Spanning over 14 years, the Equation Group has infected thousands of targets with malware that rewrites hard disk firmware and hijacks the running of operating systems. The group is suspected to have access to a very, very large pool of resources and is definitely a nation-sponsored effort; although Kaspersky is unwilling to point fingers at any potential culprits.
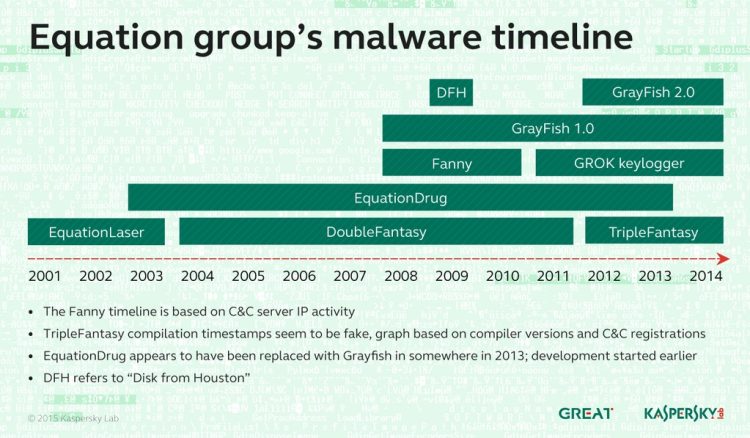
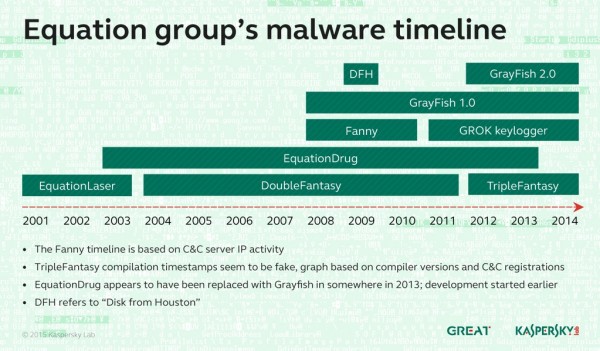
Equation Group uses a range of tools to accomplish its tasks, and even takes steps to avoid targeting systems that have no intelligence value. There are six known malware modules used, each being used alone or in tandem with one another. Kaspersky has dubbed them: EquationLaser, EquationDrug, DoubleFantasy, TripleFantasy, Fanny and GrayFish.
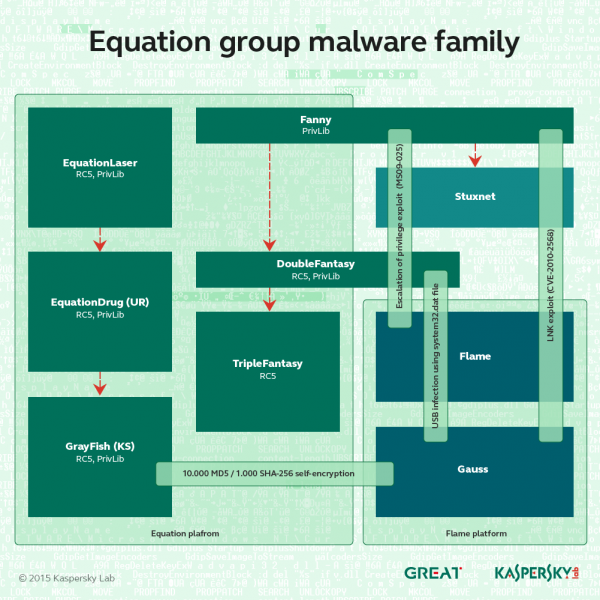
Of these malware, it is GrayFish that is the most dangerous as it is capable of hijacking the boot sequence and taking over the operating system. The malware writes itself into the boot record, and takes control of the running of Windows at every stage. Effectively, the malware is running the operating system for the user.
It avoids detection by encrypting and hiding the files in the computer registry; these files are decrypted and executed as needed, making it very difficult for anti-virus programmes to detect them. More importantly, GrayFish has also been discovered to be writing itself into the firmware of storage devices. This prevents it from being erased by formatting the hard disk, and tests have shown that it can resurrect itself from a military grade wipe.
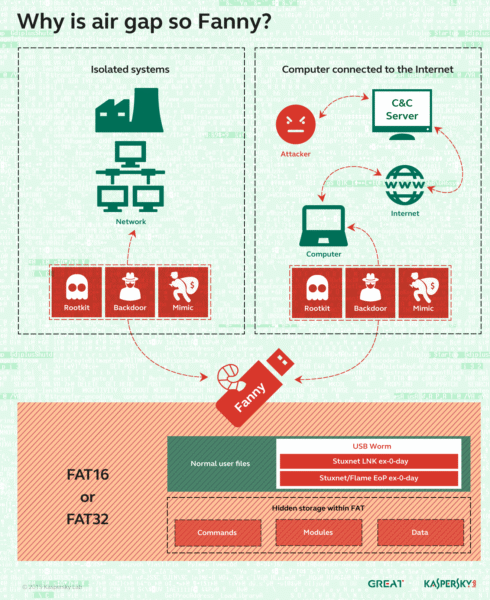
Air-gapped systems have also been infiltrated by Equation Group as the Fanny malware has been detected on USB drives. The malware would hide in a hidden storage area on the drive, and execute itself when plugged into a system. It could also save instructions to be executed if the infected system ever gained an internet connection.
The Equation Group’s delivery methods also included some interestingly low tech methods that indicate that the campaign has access to many other services as well. At least two incidents of packages being intercepted and replaced with malware-laden versions have been discovered; showing that the group is perfectly capable of penetrating postal and courier services as well.
Connecting this malware is a massive sprawling network of 300 domains on 100 servers. A number far greater than any cyber-criminal has ever been known to use. The servers are hosted in multiple countries, including the US, UK, Italy, Germany, Netherlands, Panama, Costa Rica, Malaysia, Colombia and Czech Republic.
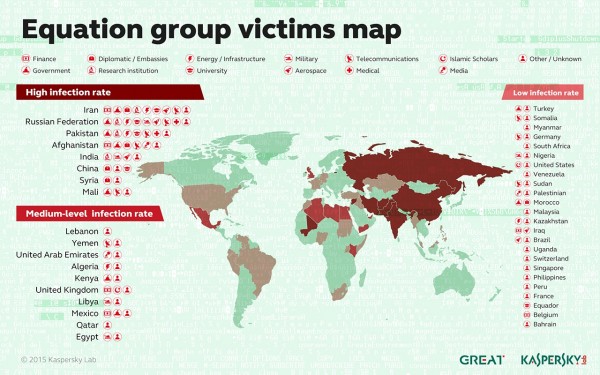
The victims were mainly in Iran, Russia, Pakistan, Afghanistan, China, Mali, Syria, Yemen and Algeria. Many sectors were targeted, including telecoms, government services, nuclear research, financial institutions, and even Islamic scholars.
While Kaspersky has not explicitly said that this was the work of the American National Security Agency, Reuters has independently confirmed with former NSA employees that this campaign was being developed at the agency. The NSA itself has refused to comment on the matter.
This is possibly the most sophisticated cyber-espionage effort ever known, and it still managed to go undetected for 14 years. While there have been a large number of detections made now, the each piece of malware has a built in self-destruct mechanism; which means that the actual number of victims could easily be in the tens of thousands.