Just about a week after the Wirelurker malware in iOS was discovered, Apple’s mobile operating system is now facing yet another vulnerability called “Masque Attack”. As its name suggests, when infected, the attack will mask itself as an existing app, making it almost impossible to discover while it sits there quietly collecting all your personal information and even banking data.
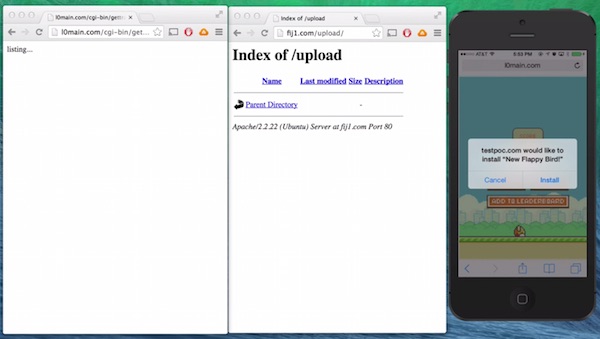
The attack was discovered by a security research company called FireEye and it works by trying to make users install an app outside of the App Store. As shown in the demo video below, the user received an SMS telling them to try out a “New Flappy Bird” game and once clicked, he/she will be prompted to install an app. The app isn’t Flappy Bird of course, instead, it’s a fake Gmail app that installs directly over the real Gmail app.
Masque Attack can replace apps installed from the App Store like banking and email apps. This means that it will stay on your phone undetected, collecting confidential information such as banking details, emails, addresses and such. According to FireEye, the attack works on iOS 7.1.1, 7.1.2, 8.0, 8.1 and even the beta version of iOS 8.1.1.
Of course, in order for Masque Attack to work, the user will have to install iOS provisioning profiles, which are commonly used for beta testing or for companies to distribute apps to their employees. This means that you should never ever install profiles onto your iOS device, unless you are completely sure that it’s legitimate.
Do you have a profile installed on your iOS device? Open up the Settings app, hit General, scroll down to Profile to see what configuration profile you have installed, and remove all the unnecessary ones – unless you do beta testing for apps or your company requires you to install certain apps from the company, I don’t see a reason to have a profile installed. Even then, make sure that it’s verified.
(Source: FireEye via: MacRumors)
Follow us on Instagram, Facebook, Twitter or Telegram for more updates and breaking news.